The Complete Guide to Spy Gadgets and Personal Security: Hidden Cameras, GPS Trackers, and Privacy Protection

Table of Contents
- Introduction: Privacy and Security in the Digital Age
- 1. Understanding Spy Gadgets and Surveillance Technology
- 2. Types of Hidden Cameras and Recording Devices
- 3. GPS Trackers: Legitimate Uses and Applications
- 4. Detecting Hidden Cameras and Surveillance Devices
- 5. Personal Security Devices and Alarms
- 6. Smart Locks and Access Control Systems
- 7. Privacy Protection Tools and Techniques
- 8. Legal and Ethical Considerations
- 9. Travel Safety and Hotel Security
- 10. Choosing Quality Security Equipment
- Conclusion: Taking Control of Your Security
- Frequently Asked Questions
Introduction: Privacy and Security in the Digital Age
We live in an era of unprecedented technological advancement where the boundaries between security and surveillance have become increasingly blurred. The same devices designed to protect us—security cameras, tracking systems, monitoring tools—can also be used to invade our privacy. Understanding this duality is essential for anyone navigating modern life, whether you’re a parent wanting to monitor your home, a business owner protecting assets, a traveler concerned about privacy in hotels, or simply someone who values personal security and wants to safeguard against unauthorized surveillance.
The global personal security market has exploded in recent years, now exceeding $120 billion annually and growing at unprecedented rates. This growth reflects increasing awareness of security threats, technological accessibility making sophisticated devices affordable, rising concerns about privacy invasion, the need for remote monitoring solutions, and growing acceptance of personal security measures. What was once the domain of professional investigators and government agencies is now accessible to everyone—hidden cameras smaller than buttons, GPS trackers lasting months on single charges, devices detecting surveillance equipment, and countless other tools that seemed like science fiction just decades ago.
But this accessibility creates complex questions and responsibilities. When does legitimate security cross into invasive surveillance? How do you protect yourself from unwanted monitoring? What legal boundaries govern these technologies? How do you choose reliable devices from countless options flooding the marketplace? These questions don’t have simple answers, but understanding the landscape empowers you to make informed decisions balancing security needs with ethical considerations and legal requirements.
While the following demonstration showcases some of the most advanced spy gadgets in action, the real security strategies and privacy protection secrets lie in the exclusive details found further down in this article—insights you likely haven’t discovered yet :
The reality is that surveillance technology exists all around us, whether we acknowledge it or not. Security cameras monitor public spaces, smartphones track our locations, smart home devices listen for commands, and countless other systems collect data about our movements, habits, and activities. Some of this surveillance serves legitimate purposes—deterring crime, finding lost items, ensuring child safety, protecting property. Other surveillance crosses ethical and legal boundaries, invading privacy without consent or justification.
This comprehensive guide explores both sides of this technological coin. We examine security devices you might choose to deploy for legitimate protection purposes—home security cameras, GPS trackers for vehicles or valuable items, personal safety alarms, smart locks controlling access. We also cover counter-surveillance tools helping you detect and prevent unauthorized monitoring—camera detectors, signal jammers, privacy screens, and techniques for identifying hidden surveillance equipment. Throughout, we emphasize legal and ethical considerations, helping you navigate this complex landscape responsibly.
Understanding these technologies serves multiple purposes beyond just using them. Knowledge protects you from unwanted surveillance—recognizing how hidden cameras work helps you spot them in unfamiliar environments. Understanding GPS trackers helps you detect if someone is tracking your movements without consent. Familiarity with surveillance techniques empowers you to take appropriate countermeasures protecting your privacy. This isn’t about paranoia; it’s about informed awareness giving you control over your personal security and privacy.
The guide addresses legitimate use cases where security devices provide genuine value. Parents monitoring their homes while at work or checking on elderly relatives remotely. Business owners protecting inventory and deterring theft. Travelers concerned about Airbnb hosts or hotel rooms potentially containing hidden cameras. Vehicle owners wanting to track their cars in case of theft. People living alone wanting additional security through monitored entry systems. These scenarios represent appropriate, legal uses of surveillance technology that enhance safety and provide peace of mind.
We also examine the darker side—unauthorized surveillance, privacy invasion, and the growing problem of hidden cameras in private spaces. Recent years have seen disturbing increases in reports of hidden cameras discovered in hotel rooms, changing areas, bathrooms, and other private spaces. Understanding how these devices work, where they’re commonly hidden, and how to detect them has become essential knowledge for anyone traveling or staying in unfamiliar accommodations. The techniques we cover aren’t just theoretical—they’re practical methods you can implement immediately to protect yourself.
Technology continues advancing at breakneck pace, making surveillance devices smaller, more powerful, and easier to conceal. What required briefcase-sized equipment decades ago now fits inside everyday objects—pens, clocks, phone chargers, smoke detectors, even clothing buttons. Battery technology improvements allow devices operating for days or weeks without recharging. Wireless connectivity enables real-time monitoring from anywhere globally. These advances provide genuine security benefits but also create new privacy challenges requiring vigilance and knowledge.
The goal isn’t to make you paranoid about surveillance—most people will never encounter malicious hidden surveillance in their daily lives. Rather, it’s to provide comprehensive knowledge empowering informed decisions about personal security while protecting against potential privacy invasions. Understanding these technologies demystifies them, reducing anxiety while providing practical tools for legitimate security needs and privacy protection.
Whether you’re considering purchasing security devices for home or personal protection, concerned about privacy in an increasingly surveilled world, traveling frequently and wanting to ensure accommodation privacy, responsible for security in professional settings, or simply curious about surveillance technology and counter-surveillance techniques, this guide provides the comprehensive information you need to navigate these issues intelligently and responsibly.
Privacy and security aren’t opposing forces—they’re complementary needs that, when properly balanced, enable us to live safely while maintaining personal autonomy and dignity. The technologies we discuss can serve either purpose depending on how they’re deployed. Our responsibility is understanding these tools thoroughly enough to use them ethically, recognize when they’re being misused, and take appropriate actions protecting ourselves and respecting others. Let’s begin exploring this fascinating and important landscape together.

1. Understanding Spy Gadgets and Surveillance Technology
The term “spy gadgets” encompasses vast array of devices designed for covert monitoring, tracking, and information gathering. Understanding what these devices are, how they function, and their intended versus potential misuses provides essential foundation for both deploying security equipment responsibly and protecting yourself from unauthorized surveillance.
The Evolution of Surveillance Technology
Surveillance devices have existed for centuries in various forms, but technological advancement over recent decades has transformed them beyond recognition. Early surveillance required obvious, bulky equipment—large cameras, visible recording devices, wired microphones. Modern surveillance technology leverages miniaturization, wireless connectivity, extended battery life, and improved image and audio quality, creating devices that are virtually undetectable without specialized knowledge and equipment.
This miniaturization represents perhaps the most significant development. Contemporary hidden cameras can be smaller than shirt buttons while recording high-definition video. GPS trackers fit inside key fobs or underneath vehicle wheel wells, operating for months on single charges. Audio recording devices disguise themselves as everyday objects—pens, USB drives, power banks—capturing conversations with remarkable clarity. The technological sophistication available to consumers today exceeds what government intelligence agencies possessed just two decades ago.
Wireless connectivity revolutionized surveillance by eliminating telltale wires and enabling real-time remote monitoring. Early hidden cameras required physical connection to recording devices or monitors, making them easier to detect and limiting placement options. Modern WiFi and cellular-enabled cameras transmit footage directly to smartphones or cloud storage, allowing monitoring from anywhere globally. This convenience serves legitimate security purposes but also facilitates privacy invasion when devices are deployed without consent.
Categories of Surveillance Devices
Surveillance technology broadly divides into several categories, each serving different monitoring purposes:
Visual surveillance devices capture images or video, ranging from obvious security cameras to covert hidden cameras disguised as everyday objects. These devices vary enormously in sophistication—from basic cameras recording to local storage, to advanced systems with motion detection, night vision, and real-time streaming capabilities. Legitimate uses include home security monitoring, baby monitoring, and business premises protection. Illegitimate uses involve unauthorized recording in private spaces like bathrooms, bedrooms, or changing areas.
Audio surveillance devices record conversations and sounds, from basic voice recorders to sophisticated systems capturing audio from significant distances. Modern devices offer excellent sound quality despite tiny sizes, with some capable of filtering background noise and enhancing target audio. Legitimate applications include recording lectures, meetings, or personal notes. Misuse involves unauthorized recording of private conversations violating consent laws in many jurisdictions.
Tracking devices monitor location and movement, primarily GPS trackers but also including RFID tags and other positioning technologies. These devices attach to vehicles, belongings, or even people, transmitting location data to monitoring systems. Legitimate uses include fleet management, asset tracking, finding lost items, and monitoring children or elderly family members with their knowledge and consent. Misuse involves tracking people without consent, which may constitute stalking or harassment.
Counter-surveillance devices help detect and defeat unauthorized monitoring, including camera detectors, RF signal detectors, GPS detector, and various privacy protection tools. These devices serve individuals concerned about privacy invasion, security professionals conducting sweeps, and anyone wanting assurance that private spaces remain private.
How Modern Surveillance Devices Work
Understanding the technical operation of surveillance devices helps you both deploy them effectively for legitimate purposes and detect them when concerned about unauthorized monitoring.
Hidden cameras capture video through tiny lenses, often no larger than pinhole. The lens focuses light onto image sensors—typically CMOS or CCD sensors similar to those in smartphones—which convert optical information into digital data. This data is then either stored locally on microSD cards, transmitted wirelessly to remote devices, or both. Many modern hidden cameras include motion detection, activating recording only when movement occurs, dramatically extending battery life and reducing storage needs.
Power sources vary significantly. Some devices connect to electrical outlets, providing unlimited operation but requiring access to power and potentially revealing themselves through cords or unusual placement of everyday objects near outlets. Battery-powered devices offer more flexible placement but require periodic recharging or battery replacement. Some ingenious designs incorporate themselves into functional objects that naturally connect to power—USB chargers, alarm clocks, smoke detectors—providing both power source and perfect concealment.
Wireless transmission uses WiFi, Bluetooth, or cellular connections sending captured footage to remote devices. WiFi-enabled cameras connect to local networks, accessible via apps or web interfaces from anywhere with internet access. Cellular cameras use SIM cards and mobile data, functioning independently of local networks—useful for monitoring locations lacking WiFi but requiring ongoing data plan costs. The wireless signals these devices emit can be detected using RF signal detectors, one method for discovering hidden surveillance.
GPS trackers determine location using signals from GPS satellites, typically receiving signals from multiple satellites and triangulating precise position. This location data is then transmitted via cellular networks to tracking platforms accessible through apps or websites. Advanced trackers include features like geofencing (alerts when devices enter or leave designated areas), movement detection (activating only when motion occurs to preserve battery), and historical tracking (recording movement patterns over time). Real-time trackers provide current location updates, while passive trackers store location data for later retrieval.
Shop on AliExpress via link: wholesale-hidden-camera
Legitimate Applications vs. Privacy Concerns
The same technology serving legitimate security and safety purposes can be misused for privacy invasion, making understanding appropriate applications crucial.
Legitimate home security represents the most common appropriate use. Homeowners installing visible security cameras around property perimeters deter criminals and provide evidence if crimes occur. Parents using baby monitors or nanny cams (disclosed to caregivers) ensure child safety. These applications protect people and property while respecting privacy through appropriate placement and necessary consent.
Asset tracking helps businesses monitor vehicles, equipment, and inventory. Delivery companies track fleet locations optimizing routes and ensuring accountability. Construction companies monitor expensive equipment preventing theft. Personal uses include tracking vehicles in case of theft or monitoring valuable items during travel. These applications track objects, not people without consent, respecting privacy boundaries.
Elder care monitoring helps families ensure aging relatives’ safety while respecting their dignity. Medical alert systems, motion sensors, and monitoring cameras (installed with consent and focused on safety rather than surveillance) provide peace of mind for families while allowing elderly individuals maximum independence. The key is transparency, consent, and focusing monitoring on safety rather than invasive observation of private activities.
Child safety applications include GPS trackers in children’s bags or watches (age-appropriate and explained to children), monitoring devices ensuring young children don’t leave designated safe areas, and communication devices allowing contact in emergencies. These tools balance safety concerns with age-appropriate privacy, evolving as children mature and require less monitoring.
Privacy violations occur when surveillance devices are deployed without consent in spaces where privacy is expected—bathrooms, bedrooms, changing rooms, private residences. Recent years have seen disturbing increases in hidden camera discoveries in Airbnb rentals, hotel rooms, and other accommodations. These violations aren’t just unethical; they’re illegal in most jurisdictions, potentially constituting serious crimes with substantial legal consequences.
The ethical line is generally clear: surveillance in public spaces or on property you own with appropriate disclosure is legitimate; covert surveillance in private spaces where people have reasonable privacy expectations is not. When monitoring employees or guests, disclosure and consent become essential. When using tracking devices, ensuring the person or property owner knows about and consents to tracking is crucial unless you’re the property owner tracking your own belongings.
2. Types of Hidden Cameras and Recording Devices
Hidden cameras come in countless forms, each designed for specific applications and concealment methods. Understanding different types helps you choose appropriate devices for legitimate security needs while also recognizing potential hidden surveillance in unfamiliar environments.
Disguised Object Cameras
The most common hidden cameras disguise themselves as everyday functional objects, allowing them to hide in plain sight while serving dual purposes.
Clock cameras represent popular choices for home monitoring, functioning as actual alarm clocks while incorporating tiny cameras behind clock faces or within plastic housings. These devices naturally belong on bedside tables, desks, or shelves, making placement unobtrusive. Quality models include night vision for low-light recording, motion detection to preserve storage and battery life, and WiFi connectivity for remote viewing. Battery-powered versions offer flexible placement while AC-powered models provide unlimited operation.
Smoke detector cameras capitalize on the fact that smoke detectors are expected ceiling-mounted devices that nobody examines closely. Cameras hide within detector housings, providing overhead views of rooms. Some are functional smoke detectors with integrated cameras; others are camera-only devices designed to resemble detectors. Their elevated position offers excellent vantage points for room monitoring, though ceiling mounting may require more effort than simple placement of other devices.
USB charger cameras combine universal power adapter functionality with hidden cameras, perfect for monitoring while providing legitimate purpose. These devices plug into outlets like normal chargers, with cameras hidden behind small holes in the plastic housing. They can charge devices normally while recording continuously or only when motion is detected. The ubiquity of phone chargers makes these devices extremely inconspicuous—nobody questions seeing chargers plugged into outlets.
Pen cameras incorporate tiny cameras into functioning pens, popular for mobile recording situations. While actually writing with these pens, you can record meetings, lectures, or any situation where traditional cameras would be obvious or inappropriate. Quality pen cameras offer several hours of battery life and sufficient storage for extended recording sessions. Some include one-button operation for easy covert activation.
Picture frame cameras hide behind decorative picture frames, allowing room monitoring while displaying actual photos. Cameras position behind small holes in frames or within frame housings, virtually invisible to casual observation. These devices work well in bedrooms, living rooms, or offices where picture frames naturally belong. Digital frame versions add functionality, displaying rotating images while recording.
Wearable Cameras
Wearable cameras allow mobile recording from user’s perspective, popular for security professionals, investigators, and situations requiring evidence gathering.
Button cameras disguise themselves as actual clothing buttons, allowing completely covert recording during face-to-face interactions. These tiny devices capture surprisingly good video given their minimal size, though battery life is limited due to size constraints. Some include tiny cables connecting to battery packs worn elsewhere on body, extending operation time. Quality button cameras include wide-angle lenses capturing expansive fields of view despite fixed positioning.
Glasses cameras integrate into functioning eyeglasses or sunglasses, recording from wearer’s natural eye level. Modern versions look essentially identical to regular glasses, making them very difficult to detect. Battery life typically allows several hours of continuous recording, sufficient for most applications. Some models include removable storage or wireless transmission capabilities. These devices work excellently for recording interactions, gathering evidence, or documenting situations requiring hands-free recording.
Watch cameras incorporate into functioning watches or fitness trackers, providing another wearable recording option. Cameras typically position where watch faces normally sit, pointing forward when hand is raised or positioned naturally during conversations. Battery constraints limit recording time, and lens positioning can be challenging for capturing desired angles. However, they offer very covert recording capabilities in casual settings.
Miniature and Professional Cameras
For situations requiring ultimate concealment or professional-grade capabilities, specialized miniature and professional surveillance cameras offer advanced options.
Pinhole cameras reduce camera mechanisms to absolute minimum sizes, with lenses literally the size of pinholes. These cameras can hide virtually anywhere—inside walls, behind tiny drilled holes, within objects too small for standard cameras. They require external recording and power systems, making installation more complex, but offer unmatched concealment. Professional installation typically involves running cables through walls or ceilings, hiding recording equipment in inaccessible locations.
WiFi mini cameras represent fully self-contained units incredibly small—some no larger than dice—but including camera, battery, processor, and wireless transmission capabilities. These devices operate independently, connecting to WiFi networks and streaming video to smartphones or cloud storage. Battery life varies from hours to days depending on usage patterns and battery size. Their tiny dimensions allow hiding in countless locations, though wireless transmission can be detected using RF signal detectors.
Motion-activated cameras preserve battery and storage by recording only when movement occurs. This feature dramatically extends operation time for battery-powered devices while reducing the amount of footage requiring review. Sensitivity adjustments prevent false triggers from minor movements like curtains shifting or pets passing by. Most modern hidden cameras include motion detection as standard feature.
Night vision cameras capture clear footage in complete darkness using infrared illumination invisible to human eyes. LEDs emitting infrared light surround camera lenses, illuminating scenes without visible light. The captured infrared-sensitive footage appears as grayscale video showing clear details despite darkness. This capability is essential for 24-hour monitoring situations where leaving lights on would be obvious or impractical. Some night vision cameras include IR illumination so subtle it doesn’t create the telltale red glow associated with cheaper night vision equipment.
Shop on AliExpress via link: wholesale-spy-camera
Audio Recording Devices
While technically separate from cameras, audio recording devices often complement visual surveillance and deserve discussion.
Voice-activated recorders begin recording only when voices or sounds exceed certain thresholds, dramatically extending operation time on single batteries. Modern devices offer excellent audio quality, with some including directional microphones focusing on specific sound sources while filtering ambient noise. Battery life can extend to days or even weeks in voice-activated mode, compared to hours in continuous recording mode.
Disguised audio recorders hide within everyday objects—USB drives, power banks, car key fobs, watches—allowing covert audio capture in countless situations. These devices typically offer simpler operation than cameras, requiring just power button presses to begin recording. Storage capacity allows many hours of audio recording, and battery life often exceeds camera alternatives due to lower power consumption.
Understanding these various camera and recorder types serves dual purposes—helping you select appropriate devices for legitimate security applications while also informing you about what to look for when concerned about unauthorized surveillance. The same features making these devices effective for security also make them potential privacy threats when misused, emphasizing the importance of ethical, legal use and vigilance in unfamiliar private spaces.

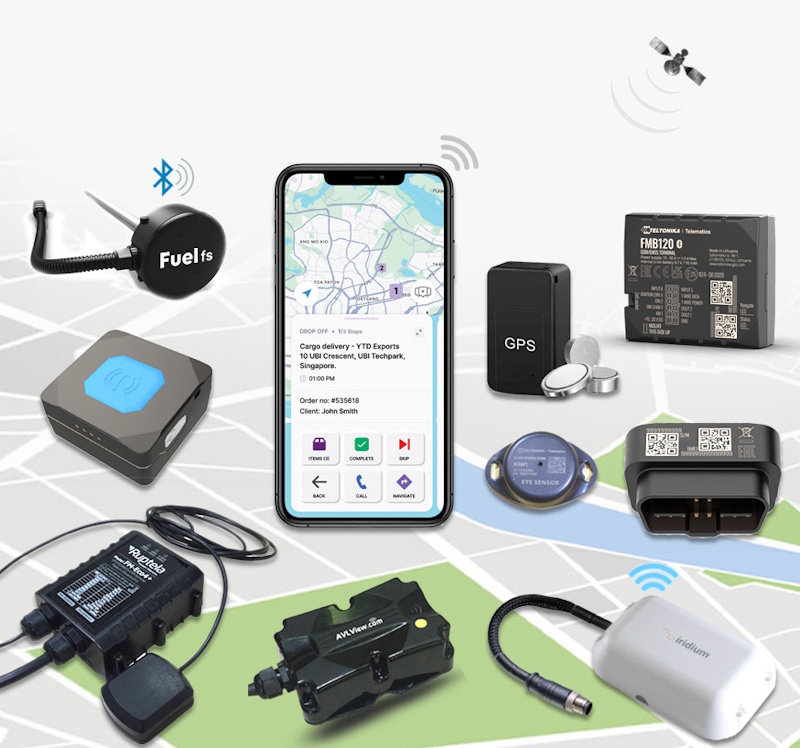
3. GPS Trackers: Legitimate Uses and Applications
GPS tracking technology has become remarkably accessible and affordable, enabling numerous legitimate applications for personal security, asset protection, and peace of mind. Understanding how these devices work and their appropriate uses helps you leverage tracking technology effectively while respecting privacy boundaries.
How GPS Trackers Work
GPS trackers determine location by receiving signals from multiple GPS satellites orbiting Earth. Each satellite continuously broadcasts signals including satellite position and precise time. GPS receivers in tracking devices calculate distances to multiple satellites based on signal travel times, then use triangulation determining precise location—typically accurate within 10-30 feet under good conditions. This location data is then either stored locally for later retrieval (passive tracking) or transmitted in real-time to monitoring platforms via cellular networks (active tracking).
Modern GPS trackers include sophisticated features beyond basic location reporting. Geofencing creates virtual boundaries around specific locations, triggering alerts when tracked devices enter or leave designated areas—useful for ensuring children stay within safe zones or monitoring if vehicles leave expected locations. Movement detection activates tracking only when devices move, dramatically extending battery life by not transmitting when stationary. Speed alerts notify when tracked items exceed set velocities, useful for monitoring driving behavior or detecting unauthorized vehicle use. Historical tracking records movement patterns over time, providing comprehensive activity logs.
Vehicle Tracking Applications
Vehicle tracking represents one of the most common legitimate GPS tracker uses, serving various purposes for personal and commercial applications.
Theft recovery remains a primary motivation for personal vehicle tracking. GPS trackers hidden within vehicles allow owners to locate stolen cars quickly, dramatically increasing recovery chances. Many insurance companies offer premium discounts for vehicles with approved tracking systems, recognizing their theft deterrence and recovery benefits. Some trackers include additional features like remote engine immobilization, preventing stolen vehicles from being driven once theft is detected.
Fleet management for businesses relies heavily on GPS tracking, allowing companies to monitor vehicle locations, optimize routing, verify employees are following assigned routes, track mileage for reimbursement and tax purposes, and improve customer service through accurate arrival time estimates. These systems generate comprehensive reports analyzing fuel efficiency, idle time, speeding incidents, and other factors affecting operating costs. The ROI for commercial fleet tracking is well-documented, with most businesses reporting significant savings offsetting system costs within months.
Teen driver monitoring helps parents ensure young drivers’ safety without constant direct supervision. GPS trackers combined with vehicle monitoring systems report speeding, hard braking, rapid acceleration, and other risky driving behaviors. Geofencing ensures teens stay within approved areas, while curfew alerts notify parents if vehicles operate during restricted hours. While privacy considerations are important, most parents and safety experts agree that monitoring teen drivers during their high-risk early driving years is appropriate and beneficial.
Personal and Asset Tracking
Beyond vehicles, GPS trackers serve numerous personal security and asset protection purposes.
Child safety tracking provides parents peace of mind through age-appropriate monitoring. GPS-enabled watches or devices in children’s backpacks allow location verification, ensuring children arrive safely at destinations and don’t wander into dangerous areas. Geofencing around schools, homes, and approved locations creates safety zones with alerts if children leave boundaries. As children mature, these systems can transition to location-sharing arrangements respecting growing independence while maintaining safety connections.
Elderly care tracking helps families ensure aging relatives’ safety, particularly those with dementia or other conditions causing confusion or wandering. GPS-enabled devices in clothing, jewelry, or carried items allow quick location determination if loved ones become disoriented or lost. These systems balance safety needs with dignity, providing security without invasive constant supervision. Medical alert systems increasingly incorporate GPS tracking, enabling emergency responders to locate individuals even if they cannot communicate their positions.
Pet tracking has exploded in popularity as GPS technology has miniaturized sufficiently for collar-mounted devices. Lost pets represent heartbreaking situations for owners; GPS tracking dramatically increases recovery chances by providing current location data rather than relying on traditional found-pet networks. Activity monitoring features in some pet trackers also provide health insights, detecting unusual behavior patterns potentially indicating medical issues.
Valuable item tracking protects expensive equipment, luggage during travel, bikes, tools, and other high-value property. Small GPS trackers hidden within or attached to valuables allow location monitoring and theft recovery. Geofencing alerts owners if items leave expected locations, enabling quick response to potential theft. Travel applications include luggage tracking ensuring bags aren’t lost or stolen during flights and accommodation transitions.
Choosing Quality GPS Trackers
Selecting appropriate GPS trackers requires evaluating several key factors affecting performance and suitability for intended applications.
Battery life varies enormously across devices. Real-time trackers transmitting location continuously drain batteries quickly, typically lasting days to a week before requiring recharge. Movement-activated trackers conserve power by transmitting only when devices move, extending battery life to weeks or months. Some trackers include replaceable batteries; others require charging via USB. Consider usage patterns when evaluating battery specifications—real-time tracking is essential for some applications but unnecessary for others where periodic location checks suffice.
Size and concealment affect tracker deployment options. Smaller devices hide more easily but typically sacrifice battery capacity. Magnetic mounting enables quick attachment to vehicle undercarriages without permanent installation. Some trackers are waterproof, essential for outdoor applications where weather exposure occurs. Consider where you’ll place trackers and any concealment requirements when evaluating size options.
Connectivity methods determine how location data reaches monitoring platforms. Cellular trackers use SIM cards and mobile networks, functioning independently but requiring monthly or annual service plans. Fees typically range from $10-30 monthly depending on update frequency and features. Some trackers include first-year service with device purchase. WiFi-based trackers work within range of known WiFi networks, limiting utility for mobile tracking but working well for home-based applications. Bluetooth trackers offer very limited range but very long battery life, useful for finding lost items nearby rather than true GPS tracking.
Subscription costs represent ongoing expenses beyond initial device purchase. Most GPS trackers require service subscriptions covering cellular data for location transmission. Compare total cost of ownership including both device and subscription fees when evaluating options. Some inexpensive trackers have expensive subscriptions; others charge more upfront but include extended service periods or offer more affordable ongoing plans.
Shop on AliExpress via link: wholesale-gps-tracker
Legal and Ethical GPS Tracking Considerations
GPS tracking raises important legal and ethical questions requiring careful consideration before deployment.
Tracking vehicles you own is generally legal, though tracking spouses without consent may violate privacy laws depending on jurisdiction even if you co-own vehicles. Tracking employees during work hours in company vehicles is typically legal with proper disclosure, though laws vary by location. Always research specific regulations governing your situation before deploying GPS tracking.
Tracking other people without consent is illegal in most jurisdictions and may constitute stalking or harassment. Even if relationships or situations make tracking seem justified to you, unauthorized tracking violates privacy rights and often breaks laws. If you’re concerned about someone’s safety, communicate openly rather than resorting to covert tracking.
Children and dependent adults represent special cases where tracking is generally accepted with appropriate age and situation considerations. Minors under parental authority can be tracked, though balancing safety with age-appropriate privacy remains important. Elderly relatives may require tracking for safety, ideally with their knowledge and consent when cognitive abilities allow understanding. Always prioritize dignity and minimum necessary monitoring even in dependent care situations.
GPS tracking technology provides powerful capabilities for legitimate security, safety, and asset protection purposes. Understanding these applications and respecting legal and ethical boundaries enables you to leverage tracking benefits responsibly while avoiding privacy violations that harm others and potentially create legal consequences for you.
4. Detecting Hidden Cameras and Surveillance Devices
Understanding how to detect hidden cameras and unauthorized surveillance equipment has become essential knowledge for anyone traveling, staying in unfamiliar accommodations, or concerned about privacy in private spaces. While most people will never encounter malicious hidden surveillance, knowing detection techniques provides peace of mind and practical protection when needed.
Why Camera Detection Matters
Recent years have seen disturbing increases in hidden camera discoveries in hotels, Airbnb rentals, changing rooms, bathrooms, and other spaces where privacy is expected and legally protected. While these incidents represent a tiny percentage of accommodations, the violation is severe enough that understanding detection methods is worthwhile. Beyond accommodation scenarios, hidden cameras have been discovered in workplaces, restrooms, and other locations where unauthorized surveillance violates privacy rights and often breaks laws.
Camera detection isn’t about paranoia—it’s about informed awareness and practical skills providing genuine privacy protection. The techniques we discuss require no special expertise and minimal equipment, making them accessible to anyone concerned about potential surveillance. Understanding these methods also makes you more conscious of your surroundings generally, which enhances security awareness in multiple contexts beyond just camera detection.
Visual Inspection Techniques
The most accessible detection method involves careful visual inspection of spaces where you expect privacy. While hidden cameras are designed for concealment, physical placement requirements create tells that careful observation can reveal.
Look for unusual objects or items positioned to view beds, bathrooms, changing areas, or other private spaces. Ask yourself if objects’ positions make sense—why is that clock facing the bed rather than positioned for easy viewing? Why is there a smoke detector in this small bathroom when building codes wouldn’t require it? Why does that electrical outlet have an unusual bulge or look slightly different from others? Trust your instincts when something feels wrong about objects’ positioning or appearance.
Check for small holes in walls, ceilings, furniture, decorations, or other surfaces. Pinhole cameras require only tiny openings for lenses, easily overlooked during casual observation but visible during careful inspection. Pay special attention to areas facing beds, showers, toilets, or changing areas. Use your phone’s flashlight shining at angles across surfaces—sometimes side-lighting reveals small holes not visible under normal lighting.
Examine everyday objects that seem out of place or unnecessary. A digital clock in a room with another clock nearby? A USB charger plugged in despite no devices charging? Picture frames positioned to face private areas rather than sitting areas? Books on shelves positioned at odd angles? Air fresheners in unusual locations? These could be innocent, but they warrant closer inspection when positioned to view private areas.
Inspect mirrors, particularly in bathrooms and bedrooms. Two-way mirrors allow viewing from one side while appearing as normal mirrors from the other. Test mirrors by placing your fingertip against the glass—in normal mirrors, a gap exists between your finger and its reflection because the reflective coating is behind the glass. In two-way mirrors, your finger and reflection touch directly because the reflective coating is on the front surface. Also check if you can see light through mirrors when rooms behind them are lit—this might indicate two-way mirrors. However, this test isn’t foolproof as modern camera technology can work with regular mirrors by positioning lenses at mirror edges or in surrounding frames.
Look for blinking lights or LED indicators visible in darkness. Many devices include status LEDs that blink during recording or wireless transmission. Turn off lights and close curtains making rooms completely dark, then look for any small lights—red, green, blue—that could indicate active electronics. Check electrical outlets, smoke detectors, clocks, and other devices for unusual indicators.
Using Smartphone Detection Methods
Your smartphone provides surprisingly effective tools for detecting certain types of hidden cameras without requiring additional equipment purchases.
Camera lens detection using phone camera exploits the fact that camera lenses reflect light distinctively. Turn off room lights or wait until dark, then use your phone’s flashlight while viewing the room through your phone camera. Slowly pan around, looking for small bright reflections that could indicate camera lenses. Camera lenses create distinctive pinpoint reflections that stand out against other reflective surfaces. This method works best in darkness and requires patience systematically checking all areas.
Infrared detection works because many hidden cameras use infrared LEDs for night vision, which are invisible to human eyes but visible to phone cameras. Most phone cameras can detect infrared light, particularly front-facing cameras which often lack IR filters. In complete darkness, point your phone camera around the room while looking at your screen—night vision camera LEDs appear as bright white or purple lights on your phone screen despite being invisible to your eyes. Check smoke detectors, clocks, vents, and other potential camera locations.
WiFi network scanning helps detect cameras connecting to local WiFi. Use network scanner apps on your phone identifying all devices connected to WiFi networks. Look for unfamiliar devices, particularly those with generic names or descriptions suggesting cameras or surveillance equipment. This method only detects WiFi-enabled cameras, missing cellular-connected or recording-only devices, but it’s easy and requires only free apps.
Professional Detection Equipment
For more thorough or professional-level detection, specialized equipment provides capabilities beyond smartphone methods.
RF signal detectors identify wireless transmissions from hidden cameras, GPS trackers, and other surveillance devices. These detectors scan radio frequencies detecting signals from devices transmitting data via WiFi, Bluetooth, cellular, or other wireless protocols. Sensitive models can detect even very weak signals, though they also pick up legitimate wireless devices like routers, phones, and smart home gadgets. Using RF detectors requires understanding how to distinguish between normal wireless activity and potential surveillance devices, usually by eliminating known sources and investigating remaining signals.
Camera lens finders use focused LED lights creating reflections specifically from camera lenses. Users view through optical viewfinders while the device’s LEDs illuminate the area—camera lenses create distinctive bright reflections visible through the viewfinder. These devices work in lit rooms, unlike the flashlight method requiring darkness, making them more convenient for thorough searches. Quality lens finders can detect lenses several feet away, including very small pinhole camera lenses.
Hidden camera detectors combine multiple detection technologies—RF detection, lens finding, magnetic field detection—into single devices providing comprehensive scanning capabilities. These professional tools cost more than basic detectors but offer superior detection rates. Some include sensitivity adjustments optimizing performance for different situations and detailed displays identifying signal strengths and types.
Shop on AliExpress via link: wholesale-camera-detector
Systematic Room Sweeps
Effective detection requires systematic approaches ensuring complete coverage rather than random checking.
Start your sweep at room entrances, working methodically in one direction covering all areas before leaving. This systematic approach prevents missing sections during unsystematic searches. Check obvious locations first—smoke detectors, clocks, electrical outlets, mirrors—before progressing to less obvious possibilities. Use your phone’s camera, flashlight, and any detection equipment you’ve acquired while carefully inspecting potential camera locations.
Pay special attention to areas facing beds, showers, toilets, and changing areas—these are where unauthorized cameras are most likely positioned to capture private activities. Check from multiple angles, as cameras might be positioned to avoid detection from typical viewing angles. Move furniture and decorations inspecting behind and underneath them. Don’t forget to check ceilings—overhead cameras provide excellent vantage points and are often overlooked.
Test electrical outlets and switches, as these common camera hiding spots connect to power sources. Remove outlet covers checking inside boxes for foreign objects or unusual wiring. Some hidden cameras disguise themselves as functioning outlets or hide within electrical boxes behind outlets. Check if outlets feel warm or show any blinking lights indicating active electronics.
Inspect ventilation grills and air vents, which provide excellent camera concealment while offering unobstructed views of rooms. Remove grill covers if possible, checking inside ducts for cameras or other devices. Cameras in vents benefit from dark backgrounds making lenses harder to spot visually but are often detectable using phone flashlight methods.
What to Do If You Find Hidden Cameras
Discovering hidden surveillance equipment requires careful response protecting your rights and safety while documenting violations.
Don’t touch or move discovered devices immediately, as you want to preserve evidence documenting their positions and characteristics. Take photos from multiple angles clearly showing devices, their positions, and context proving they’re surveillance equipment in private spaces. Note exact locations, times of discovery, and all relevant details.
Contact authorities immediately—police for criminal violations, hotel management or Airbnb for accommodation violations. Hidden cameras in private spaces violate privacy laws in most jurisdictions, constituting crimes requiring police involvement. Don’t rely solely on accommodation providers to handle situations, as they may prioritize minimizing publicity over properly addressing violations. File formal police reports creating official records.
Leave accommodations if possible after discovering hidden cameras, as staying in locations where your privacy was violated is unsafe and potentially traumatizing. Most hotels and booking platforms provide alternative accommodations in such situations. Document everything, save all communications, and consider consulting attorneys regarding potential legal actions for privacy violations.
Understanding detection techniques provides practical protection while hopefully remaining knowledge you never need to use. Most accommodations and private spaces don’t contain hidden surveillance. But having these skills provides peace of mind and genuine protection in the unfortunate event you encounter unauthorized surveillance.
5. Personal Security Devices and Alarms
Beyond surveillance detection and privacy protection, numerous personal security devices provide active protection through deterrence, alerting others to danger, or providing means to summon help quickly. These devices range from simple panic alarms to sophisticated personal security systems, offering options for various situations and security needs.
Personal Alarm Devices
Personal alarms emit loud sounds when activated, deterring attackers and alerting others to dangerous situations. These simple yet effective devices provide security for individuals walking alone, living alone, elderly people at fall risk, children traveling to school, or anyone wanting quick attention-grabbing capabilities in emergencies.
Keychain alarms attach to keys, bags, or belts, keeping them readily accessible. Activation typically involves pulling pins, pressing buttons, or breaking away magnetic connections—simple actions performable even in stressful situations. Quality alarms produce sounds exceeding 120 decibels, comparable to sirens or jet engines, extremely difficult to ignore even in noisy environments. Battery-operated designs require no charging, working reliably for months or years before needing battery replacement.
Wearable panic buttons take various forms—bracelets, pendants, clip-on devices—allowing discreet carrying while ensuring accessibility. Some connect to smartphones via Bluetooth, automatically alerting emergency contacts or services when activated. Medical alert versions include fall detection, automatically triggering alarms if devices detect falls followed by lack of movement. GPS-enabled models transmit location data along with alerts, enabling responders to locate users even if they cannot communicate verbally.
Door and Window Alarms
Entry point alarms provide simple yet effective security for homes, hotel rooms, and temporary accommodations. These devices detect when doors or windows open, triggering loud alarms deterring intrusions and alerting occupants.
Portable door alarms wedge under doors or hang from doorknobs, activating if doors open while alarms are set. Battery-powered and requiring no installation, these devices work excellently for travel security in hotel rooms or Airbnbs. Most include adjustable sensitivity preventing false alarms from normal vibrations while reliably triggering for actual entry attempts. Some include both alarm mode and chime mode, allowing notification of entries without full alarm sounds.
Window sensors attach to window frames using adhesive strips, detecting if windows open beyond set amounts. Wireless versions connect to central hubs or smartphones, enabling monitoring of multiple entry points simultaneously. Some include additional sensors detecting glass breaking, triggering alarms even if windows aren’t opened but are instead broken for entry. Battery life typically extends months before requiring replacement.
Smart home security integration allows comprehensive systems monitoring all entry points with professional monitoring services, cameras, and automated responses. While more expensive and complex than simple alarms, integrated systems provide superior security for permanent residences. Many systems allow remote monitoring and control via smartphone apps, enabling you to check security status and receive alerts anywhere.
Motion Sensor Lights and Cameras
Motion-activated lighting and surveillance combine to deter intruders while documenting any security events that do occur.
Outdoor motion lights illuminate property perimeters when movement is detected, eliminating darkness that conceals intruders while reducing energy costs compared to always-on lighting. Modern LED motion lights provide bright illumination while consuming minimal power and lasting years before requiring bulb replacement. Adjustable sensitivity and timeout durations customize performance for specific locations and needs. Solar-powered versions eliminate wiring requirements while providing sustainable operation.
Motion-activated cameras begin recording only when movement occurs, conserving storage and battery while ensuring important events are captured. Indoor and outdoor models provide comprehensive property monitoring without requiring continuous recording review. Cloud storage options enable accessing footage remotely, while local storage provides privacy and eliminates subscription costs. Many cameras include two-way audio allowing communication with visitors or potential intruders.
Safety Apps and Connected Devices
Smartphone applications and connected devices provide personal security through location sharing, emergency alerting, and safety check-ins.
Emergency alert apps allow quick notifications to designated contacts with single button presses, automatically sharing location data and situation details. Some include audio or video recording capabilities capturing evidence during emergencies. Safety walking apps provide virtual escorts, tracking your route and checking if you arrive safely at destinations, triggering alerts if trips take longer than expected or devices detect falls or accidents.
Location sharing applications allow trusted contacts to monitor your location during potentially risky situations—walking alone at night, first dates, traveling in unfamiliar areas. Temporary sharing options provide security without permanent location disclosure, expiring after set times or when destinations are reached. Two-way location sharing enables mutual awareness among friends or family members.
Wearable safety devices range from simple panic buttons to sophisticated smartwatches with fall detection, heart rate monitoring, and emergency calling capabilities. Some jewelry items incorporate panic buttons or GPS tracking in attractive, inconspicuous designs. These devices provide security without obviously advertising vulnerability.
Personal security devices work best in combination rather than isolation. Multiple security layers—alarms at entry points, motion lighting outside, personal alarms carried, safety apps on phones—create comprehensive protection addressing various threat scenarios. No single device provides complete security, but thoughtful combinations dramatically improve safety while providing peace of mind.
6. Smart Locks and Access Control Systems
Modern lock technology has evolved far beyond traditional mechanical keys, offering enhanced security, convenience, and control through smart locks and advanced access control systems. These devices provide numerous benefits for home security, property management, and personal peace of mind while introducing considerations regarding digital security and reliability.
Types of Smart Locks
Smart locks eliminate traditional keys through various authentication methods, each offering distinct advantages and limitations.
Keypad locks require numerical codes for entry, removing key-related concerns about losing keys, unauthorized key duplication, or lockouts when keys are forgotten. Multiple user codes allow different access for family members, guests, or service providers, with ability to add or delete codes easily. Temporary codes provide time-limited access—useful for guests, contractors, or rental properties—automatically expiring after set periods. Some keypad locks include traditional key backups for situations where electronic systems fail.
Bluetooth-enabled locks unlock automatically when authorized smartphones approach, providing keyless entry without requiring code input. Users simply approach doors with phones in pockets or bags; locks detect authorized devices and unlock automatically. Manual unlocking via smartphone apps provides alternative when automatic unlock doesn’t trigger. Range and sensitivity adjustments customize triggering distance preventing premature unlocking while ensuring reliable detection when desired.
WiFi-connected locks enable remote access from anywhere with internet connectivity, allowing door locking or unlocking via smartphone apps regardless of physical location. This capability facilitates letting in guests when you’re not home, ensuring doors locked after leaving, or providing access to service providers while monitoring entry. Activity logs track all locking and unlocking events with timestamps, creating comprehensive access records.
Fingerprint locks use biometric authentication, providing security through unique physical characteristics impossible to lose, share, or duplicate. Multiple fingerprint enrollment allows different family members or authorized users while preventing unauthorized access. High-quality fingerprint sensors work reliably in various conditions, though very cold or wet weather can sometimes affect recognition accuracy. Battery backup ensures operation during power outages.
Smart Lock Features and Capabilities
Modern smart locks include various features enhancing security and convenience beyond basic electronic locking.
Auto-lock functions automatically secure doors after set time periods, ensuring doors don’t remain unlocked when you forget to lock them manually. Adjustable timing accommodates different needs—quick locking for high-security situations or longer delays when carrying items in from vehicles requiring multiple trips.
Geofencing uses location services automatically locking doors when you leave home and unlocking as you approach. This automation removes need for manual control, ensuring doors lock reliably when you depart. Accuracy requirements prevent premature locking if you’re just taking out trash or prevent unlocking until you’re actually at doors rather than just nearby.
Voice control integration with Amazon Alexa, Google Assistant, or Apple HomeKit allows voice commands locking or checking door status. This hands-free control provides convenience when carrying items or when hands are otherwise occupied. Security considerations require careful setup ensuring voice commands don’t allow unauthorized access—most systems require additional authentication beyond just voice for unlocking doors.
Activity monitoring and notifications track all access events, sending smartphone alerts whenever doors lock or unlock. Detailed logs show who accessed doors, when, and through which method—codes, fingerprints, smartphones, manual keys. This awareness provides security and convenience, letting you know when children arrive home, when service providers enter, or if doors are accessed unexpectedly.
Tamper alerts detect attempts to remove locks or forced entry, immediately sending notifications and triggering built-in alarms. Some smart locks include backup power from standard batteries even during main power failure, ensuring continuous operation. Low battery warnings provide advance notice before power runs out, preventing unexpected lockouts.
Installation and Compatibility
Smart lock installation varies from simple replacement of existing deadbolts requiring no additional hardware to complex installations involving professional locksmith services.
Most smart deadbolt replacements install using existing door preparations with no drilling or modifications required. Basic tools and moderate DIY skills suffice for installation, typically taking 15-30 minutes following manufacturer instructions. Some locks maintain exterior key cylinders for traditional backup access alongside smart features, providing security if electronic systems fail.
Door compatibility considerations include door thickness, backset measurements (distance from door edge to center of deadbolt hole), and existing hardware. Most smart locks accommodate standard residential door specifications, but older doors, particularly thick doors or those with non-standard hardware, may require adaptations or professional installation.
Integration with existing smart home systems simplifies control when smart locks work with your preferred platforms—Apple HomeKit, Google Home, Amazon Alexa, Samsung SmartThings, or others. Native integration allows unified control of locks alongside other smart devices like lights, thermostats, and security cameras. Some locks work with multiple platforms; others lock into specific ecosystems.
Security Considerations
While smart locks offer numerous benefits, they introduce digital security considerations alongside physical security.
Encryption protects communication between locks, smartphones, and cloud services, preventing interception or manipulation. Strong encryption standards ensure only authorized devices can control locks. Regular firmware updates address discovered vulnerabilities, making keeping lock software current important for maintaining security.
Physical backup access through traditional keys or mechanical overrides provides security if electronic systems fail due to dead batteries, technical malfunctions, or cybersecurity issues. While convenience of keyless entry is smart locks’ main appeal, maintaining backup access methods prevents lockouts during system failures.
Password and code security requires using strong, unique combinations not easily guessed by unauthorized individuals. Avoid obvious codes like birthdates or sequential numbers. Change codes periodically and immediately after providing temporary access to guests or service providers.
Network security for WiFi-connected locks requires securing home networks with strong passwords and WPA3 encryption. Vulnerable home networks can potentially allow unauthorized access to smart locks and other connected devices. Separate networks for IoT devices including smart locks provide additional security isolation from main home networks.
Shop on AliExpress via link: wholesale-smart-lock
Smart locks represent significant advances in access control, offering genuine security improvements alongside considerable convenience benefits. Understanding their capabilities and limitations, proper installation and configuration, and maintaining good security practices maximizes their benefits while minimizing potential vulnerabilities.

7. Privacy Protection Tools and Techniques
Beyond detecting unwanted surveillance, proactive privacy protection tools and techniques help you maintain control over personal information and prevent various forms of monitoring. These range from simple physical barriers to sophisticated electronic countermeasures.
Camera Covers and Privacy Screens
The simplest privacy tools involve physical barriers blocking camera and screen viewing.
Webcam covers attach to laptops, monitors, or smartphones using sliding mechanisms that open for legitimate video calls but otherwise block camera lenses. These inexpensive accessories prevent unauthorized camera access from malware or hackers. Many laptops now include built-in camera privacy shutters, but aftermarket covers work for devices lacking integrated protection.
Privacy screen protectors attach to smartphone, tablet, or computer screens, using special films that darken screens when viewed from angles. Content remains clearly visible when viewed directly but becomes illegible from sides, preventing over-the-shoulder snooping in public spaces. These protectors work excellently for protecting sensitive information when working in cafes, airports, or other public locations where visual privacy is difficult.
Signal Blocking and Faraday Pouches
Signal blocking devices prevent wireless tracking and communication, providing privacy through isolation from wireless networks.
Faraday bags or pouches use metallic mesh fabric blocking all electromagnetic signals including cellular, WiFi, GPS, Bluetooth, and RFID. Phones placed in Faraday pouches cannot be tracked, contacted, or used as listening devices. These bags work for situations requiring complete privacy from electronic tracking—sensitive meetings, locations you don’t want tracked, or preventing forensic access to devices.
RFID-blocking wallets and passport holders prevent electronic skimming of credit cards, ID cards, and passports containing RFID chips. While actual risks from RFID skimming are debated, these inexpensive protective measures provide peace of mind for those concerned about unauthorized scanning of payment or identification information.
Privacy Software and Digital Protections
Digital privacy requires software solutions alongside physical tools.
VPN (Virtual Private Network) services encrypt internet traffic and mask IP addresses, preventing ISPs, networks, or potential attackers from monitoring online activities. VPNs provide crucial privacy when using public WiFi networks in hotels, airports, or cafes where unencrypted traffic can be intercepted. Choose reputable VPN providers with strong encryption, no-logging policies, and sufficient server infrastructure.
Encrypted messaging applications like Signal, WhatsApp (with end-to-end encryption enabled), or Telegram provide private communication preventing interception or monitoring. These apps encrypt message content so only sender and recipient can read them—not even app providers can access message content. Using encrypted messaging for sensitive communications provides significantly better privacy than standard SMS or email.
Password managers securely store login credentials, payment information, and sensitive notes using strong encryption. Using password managers enables unique, complex passwords for every account without needing to remember them all, dramatically improving security compared to reusing simple passwords across multiple services.
Two-factor authentication (2FA) adds security layer beyond passwords, requiring second form of verification—codes from authentication apps, SMS messages, or physical security keys. Enabling 2FA on accounts containing sensitive information significantly reduces unauthorized access risk even if passwords are compromised.
Secure Communication Practices
Beyond tools, practices and awareness protect privacy in various situations.
Public WiFi avoidance or using VPNs when connecting to public networks prevents traffic interception. Public WiFi networks in cafes, hotels, or airports often lack encryption, allowing others on same networks to potentially intercept your traffic. If you must use public WiFi, always use VPN encryption protecting your data.
Covering keypad when entering PINs or passwords prevents visual observation of entry codes. This simple habit protects against shoulder surfing in public spaces. Position yourself to minimize what others can see on screens when working with sensitive information.
Regular privacy settings review on social media, smartphones, and online accounts ensures you’re sharing only what you intend. Default settings often allow more data sharing than most people prefer. Periodically audit privacy settings, adjusting to minimize information disclosure.
Physical document security through shredding important documents before discarding prevents identity theft from dumpster diving or trash inspection. Financial statements, medical records, and documents containing personal information should be cross-cut shredded rather than simply thrown away intact.
Privacy protection is ongoing process rather than one-time setup. Combining appropriate tools with good practices and regular reviews of privacy settings and potential vulnerabilities maintains effective privacy protection adapted to your specific risks and circumstances.
8. Legal and Ethical Considerations
Understanding legal and ethical boundaries surrounding surveillance technology and privacy protection is crucial for anyone deploying security devices or concerned about unauthorized monitoring. Laws vary significantly across jurisdictions, but general principles apply broadly.
Surveillance and Recording Laws
Legal permissibility of recording varies dramatically based on location, recording type, and consent.
Video recording laws generally distinguish between public and private spaces. Recording in public spaces is typically legal, while recording in locations where privacy is reasonably expected—bathrooms, bedrooms, changing rooms, private residences—requires consent. Consent requirements vary by jurisdiction, with some requiring all-party consent (everyone being recorded must agree) while others allow single-party consent (only the person doing recording needs to consent).
Audio recording often has stricter regulations than video recording. Many jurisdictions prohibit recording private conversations without all parties’ consent. Some states allow single-party consent for audio recording, meaning if you’re part of conversation, you can record without informing others. Always research specific laws governing your location before recording audio, as violations can result in serious criminal charges.
Workplace surveillance generally is legal when properly disclosed to employees, though specifics vary by location. Employers typically can monitor workspaces, company computers, and work activities, but monitoring bathrooms, changing areas, or other private spaces remains prohibited. Many jurisdictions require notifying employees about monitoring policies even when surveillance is legal.
Privacy Rights and Expectations
Legal concept of “reasonable expectation of privacy” determines whether surveillance violates rights.
Private residences carry highest privacy expectations. Recording inside someone else’s home without permission violates privacy rights regardless of your relationship to that person. Even in your own home, recording guests without disclosure may violate laws depending on jurisdiction.
Bathrooms, bedrooms, and changing areas always carry privacy expectations regardless of ownership or location. Recording in these spaces without explicit consent is illegal in essentially all jurisdictions and often constitutes serious criminal offense. Hotel rooms and temporary accommodations carry same privacy protections as permanent residences.
Public spaces generally do not carry privacy expectations, though state laws vary. Recording people in parks, streets, or other public areas typically is legal, though specific regulations may restrict recordings near government buildings, schools, or other sensitive locations.
GPS Tracking Legality
Tracking laws create complex landscape varying significantly by jurisdiction and circumstances.
Vehicle tracking by owners is generally legal on vehicles they own, though tracking spouses without knowledge may violate privacy laws even in shared-ownership situations. Many jurisdictions consider secret GPS tracking without consent a form of stalking or harassment.
Employee tracking during work hours in company vehicles typically is legal with proper disclosure. However, tracking personal vehicles of employees or continuing tracking outside work hours generally requires consent and may violate privacy laws.
Tracking children and dependent adults under your care typically is legal and considered appropriate parental responsibility or dependent care. However, tracking adults without consent, even family members, may violate laws.
Tracking devices placed on others’ property without permission constitutes trespassing and potentially stalking. Finding tracking devices on your vehicle placed without authorization should be reported to police.
Penalties for Violations
Violating surveillance and privacy laws results in serious consequences including criminal charges, civil lawsuits, and professional repercussions.
Criminal penalties for illegal surveillance range from misdemeanors to felonies depending on violation severity and jurisdiction. Unauthorized recording in private spaces often constitutes felony charges carrying significant prison time. Voyeurism laws specifically address recordings intended for sexual gratification, with especially severe penalties.
Civil lawsuits for privacy invasion allow victims to seek damages from those who violated their privacy through unauthorized surveillance. Damages can be substantial, particularly when violations are egregious or deliberate. Victims may recover actual damages, emotional distress damages, and sometimes punitive damages intended to punish violators.
Professional consequences can include job loss, professional license revocation, and permanent career damage for those convicted of surveillance violations. The reputational impact often extends far beyond legal penalties.
Ethical Considerations
Beyond legality, ethical considerations should guide surveillance technology use.
Consent and disclosure represent fundamental ethical requirements. Even when legal not to disclose surveillance, ethical practice usually involves informing those being monitored. Surprise surveillance betrays trust and damages relationships even when legal.
Proportionality requires matching surveillance level to actual security needs. Extensive monitoring of employees, children, or others when minor issues arise violates ethical principles of proportionate response. Surveillance should be last resort, not first response.
Privacy respect involves recognizing others’ legitimate privacy interests even when surveillance might be legal. Just because you can monitor someone doesn’t always mean you should. Consider whether surveillance is truly necessary or if alternatives could address concerns while respecting privacy.
Purpose limitation means using surveillance only for declared legitimate purposes, not gathering information for unrelated uses. Security cameras installed for theft prevention shouldn’t be used to monitor employees’ personal conversations or activities unrelated to security concerns.
Understanding legal and ethical landscape surrounding surveillance technology protects you from serious consequences while ensuring you respect others’ legitimate rights. When in doubt, consult legal professionals familiar with privacy laws in your jurisdiction before deploying surveillance equipment or engaging in activities that might violate privacy rights.
9. Travel Safety and Hotel Security
Traveling creates unique security and privacy challenges—unfamiliar environments, temporary accommodations, and reduced control over surroundings all increase vulnerability to both security threats and privacy invasions. Understanding travel-specific security concerns and implementing appropriate protections significantly improves safety while maintaining privacy.
Hotel and Accommodation Security
Temporary accommodations present various security considerations requiring attention and preparation.
Room selection affects security significantly. Request rooms on second through sixth floors—ground floor rooms are more accessible to intruders while very high floors complicate emergency evacuations. Avoid rooms near stairwells or elevators where increased foot traffic provides cover for unauthorized access. Rooms near exits often are noisier and may provide easier escape routes for criminals.
Upon entering rooms for first time, conduct thorough security checks. Verify locks work properly, check windows and balconies for secure closures, test door chains and security latches, ensure phone works for emergency calls, locate fire exits and escape routes, and conduct camera detection sweeps if privacy is concern. This initial assessment takes just minutes but identifies potential issues before they become problems.
Use all available locks and security devices when in rooms. Engage deadbolts, security chains, and any additional locks provided. Portable door alarms add extra security, particularly in budget accommodations or unfamiliar locations. Many travelers carry their own portable door locks or security bars providing additional barriers to unauthorized entry.
Privacy Protection While Traveling
Protecting privacy requires additional vigilance in accommodations where you have limited control.
Hidden camera detection becomes particularly relevant when staying in Airbnbs, hostels, or budget hotels. Conduct thorough visual inspections focusing on areas facing beds, bathrooms, and changing areas. Use smartphone detection methods—camera lens reflection and infrared detection—to sweep rooms systematically. Pay special attention to smoke detectors, clocks, electrical outlets, mirrors, and decorations positioned to view private areas.
Cover or disconnect devices containing cameras—smart TVs, laptops, tablets—when not in use. Many modern hotel room TVs include cameras for video conferencing, which could potentially be accessed remotely. Placing opaque tape over camera lenses or draping clothing over devices provides simple protection.
Use VPNs when connecting to hotel WiFi networks, as these networks often lack strong security and can be monitored by other guests or hotel staff. Avoid accessing banking or sensitive accounts on public hotel networks, or ensure VPN protection when you must access them.
Secure valuables using hotel safes when available, though recognize these safes aren’t completely secure. For irreplaceable items, consider carrying them with you or using portable travel safes secured to fixed objects. Never leave cash, electronics, or important documents in plain sight in hotel rooms even when doors are locked.
Personal Safety While Traveling
Beyond accommodation security, travel safety requires awareness and preparation.
Share travel itineraries with trusted contacts, providing details about accommodations, transportation, and planned activities. Regular check-ins let contacts know you’re safe, while unexpected gaps in communication can trigger concern and response. Location sharing apps provide real-time location access for trusted contacts during travel.
Maintain situational awareness in unfamiliar environments. Avoid displaying expensive electronics, jewelry, or large amounts of cash. Stay in well-lit, populated areas, particularly at night. Trust your instincts—if situations or people make you uncomfortable, remove yourself rather than ignoring warning feelings.
Carry personal safety devices appropriate for your destinations. Many locations prohibit certain self-defense tools, so research regulations before traveling. Personal alarms, door alarms, and safety apps typically are permitted everywhere and provide substantial security benefits.
Transportation security requires attention when using taxis, rideshares, or public transportation. Verify vehicle and driver information matches what you’re expecting before entering. Share trip details with contacts and enable location tracking during rides. Sit in rear seats of taxis and rideshares, maintaining distance from drivers.
Protecting Belongings and Information
Travel often involves carrying important documents, electronics, and valuables requiring protection.
Document security starts before travel. Make copies of passports, IDs, credit cards, and important documents, storing copies separately from originals. Digital copies uploaded to secure cloud storage provide access if physical documents are lost or stolen. Provide copies to trusted contacts at home who can assist if documents are compromised.
Electronics protection involves backups before travel, password protection on all devices, encryption of sensitive data, and remote wipe capabilities enabled allowing you to erase devices if stolen. Avoid using public USB charging ports in airports or other public areas, as these can potentially transfer malware—use your own chargers with regular electrical outlets or portable battery packs.
Credit card security involves notifying card issuers about travel plans preventing legitimate charges from triggering fraud alerts. Consider using dedicated travel credit cards limiting potential damage if cards are compromised. Monitor accounts regularly during travel for unauthorized charges. Carry multiple payment methods in different locations ensuring access to funds if one payment method is compromised.
Cultural Considerations and Local Laws
Understanding local customs and laws regarding security, surveillance, and privacy prevents inadvertent violations.
Privacy laws vary dramatically internationally. Some countries prohibit devices that are legal elsewhere. Research destination-specific regulations regarding GPS trackers, hidden cameras, and other security devices before traveling. What’s legal security equipment at home might be illegal surveillance technology in your destination.
Photography and recording restrictions exist in many locations. Government buildings, military installations, religious sites, and certain public spaces often prohibit photography. Some countries restrict recording people without consent. Violating these rules can result in serious consequences including detention, fines, or worse.
Cultural sensitivity regarding privacy and security varies globally. Practices considered normal in some cultures might offend or alarm in others. Research cultural norms for destinations to avoid inadvertently causing offense or concern through security practices common in your home country.
Travel safely requires balancing security measures with cultural respect and legal compliance. Preparation, awareness, and appropriate security tools provide protection without creating unnecessary complications or violating local customs and regulations.

10. Choosing Quality Security Equipment
The security device marketplace offers countless products ranging from legitimate quality equipment to ineffective gimmicks. Understanding how to evaluate and select reliable security devices ensures your investments provide actual protection rather than false security sense.
Evaluating Device Quality
Several factors distinguish quality security devices from inferior alternatives.
Brand reputation and reviews provide crucial insights into reliability and performance. Established manufacturers with long market presence typically offer better quality and support than unknown brands. Read multiple reviews from verified purchasers, paying attention to long-term performance reports rather than just initial impressions. Recurring complaints about specific issues—battery life, connectivity problems, false alarms—indicate systemic quality problems.
Certification and compliance with relevant standards demonstrate devices meet minimum quality and safety requirements. Look for certifications relevant to device type—UL listings for electrical safety, FCC compliance for wireless devices, IP ratings for water resistance. Devices lacking appropriate certifications may not work as advertised or could even pose safety hazards.
Warranty coverage reflects manufacturers’ confidence in product quality. Longer warranties (one year or more) suggest devices are built to last, while very short warranties or lack of coverage indicates potential quality issues. Warranty terms matter too—comprehensive coverage including repair, replacement, and responsive customer support provides better protection than limited warranties excluding common failure modes.
Technical specifications should be evaluated carefully rather than simply comparing numbers. Higher numbers don’t always indicate better performance. Battery capacity matters less than actual runtime under normal use conditions. Camera resolution means little if lens quality or image processing is poor. Compare specifications to real-world performance reports from reviews.
Avoiding Common Pitfalls
Several common mistakes lead to purchasing ineffective or inappropriate security devices.
Overbuying features you won’t use wastes money and often introduces unnecessary complexity. Simple devices that you’ll actually use consistently provide better security than sophisticated systems that overwhelm you with features you never configure or maintain. Focus on capabilities addressing your specific needs rather than chasing every possible feature.
Underestimating ongoing costs leads to surprise expenses after initial purchases. Devices requiring subscriptions, batteries, cellular plans, or cloud storage incur costs beyond initial device prices. Calculate total cost of ownership over devices’ expected lifespans when comparing options. Sometimes higher initial costs lead to lower long-term expenses.
Ignoring compatibility with existing systems creates frustration when devices don’t work together. If you have invested in specific smart home platforms, ensure new devices integrate with your ecosystem. Standalone devices that don’t communicate with other security equipment limit overall system capabilities.
Prioritizing price over quality tempts many buyers but often leads to dissatisfaction. While budget options can work well, extremely cheap devices usually cut corners on quality, support, or features in ways that compromise effectiveness. Mid-range options often provide best value, balancing reasonable prices with quality sufficient for reliable long-term performance.
Installation and Setup Considerations
Even quality devices fail to provide security if improperly installed or configured.
Professional installation makes sense for complex systems, permanent installations, or situations where mistakes could compromise security. While DIY installation saves money, professional installers have experience ensuring devices work correctly and securely. Costs vary but typically are offset by avoiding problems from improper installation.
DIY installation works well for many devices, particularly portable security equipment, temporary installations, or straightforward devices with clear instructions. Follow manufacturer instructions carefully, take time to understand all features and settings, and test thoroughly after installation ensuring everything works as expected. Many manufacturers provide online resources, videos, and customer support helping DIY installers succeed.
Regular maintenance and testing ensures continued reliability. Batteries need replacement, firmware needs updating, devices need cleaning, and functionality needs verification. Establish maintenance schedules checking and maintaining security devices regularly. Test alarms, locks, cameras, and other devices periodically ensuring they work when needed.
Balancing Security and Privacy
Choosing security equipment requires balancing protection needs against privacy considerations.
Minimize data collection to only what’s necessary for security purposes. Avoid devices collecting and storing more information than needed. Consider local storage options rather than cloud storage when feasible, maintaining control over your data and reducing privacy risks from data breaches.
Understand data handling policies of devices and services. Read privacy policies, terms of service, and data usage information understanding how your data is collected, stored, shared, and used. Prefer manufacturers with strong privacy commitments and transparent policies over those with vague terms or concerning data practices.
Regular security updates protect devices from discovered vulnerabilities. Choose devices from manufacturers committed to ongoing support and updates. Devices no longer receiving security patches become increasingly vulnerable over time, potentially creating security weaknesses rather than providing protection.
Shop on AliExpress via link: wholesale-security-camera
Choosing quality security equipment involves research, careful evaluation, realistic assessment of needs, and ongoing attention after purchase. Investment in appropriate equipment providing reliable protection pays dividends through improved security and peace of mind, while poor choices waste money and potentially create false sense of security more dangerous than having no security equipment.
Conclusion: Taking Control of Your Security
In an era of unprecedented technological sophistication, where surveillance capabilities that once belonged exclusively to government agencies now fit in shirt buttons and everyday objects, understanding security and privacy has become essential knowledge for everyone. The devices and techniques we’ve explored serve dual purposes—enhancing legitimate security while protecting against invasive surveillance. Your challenge is navigating this landscape thoughtfully, using technology to protect yourself and loved ones while respecting others’ rights and maintaining ethical boundaries.
Security and privacy aren’t mutually exclusive or opposing forces—they’re complementary needs that, when properly balanced, enable us to live safely while maintaining personal autonomy and dignity. The same awareness that helps you select appropriate security devices for protecting your home helps you recognize when similar devices might be invading your privacy in unfamiliar locations. Knowledge about GPS trackers enables both legitimate asset protection and detection of unauthorized tracking. Understanding hidden cameras facilitates both home security and privacy protection in hotels and accommodations.
The key to navigating this complex landscape lies in informed decision-making guided by clear principles. Use surveillance technology only for legitimate purposes with appropriate consent and disclosure. Respect others’ privacy rights even when surveillance might technically be legal. Stay informed about laws governing surveillance and privacy in your jurisdiction. Implement security measures proportionate to actual risks rather than reacting from fear. Regularly evaluate and maintain security equipment ensuring continued effectiveness.
Technology continues advancing rapidly, making both security and surveillance capabilities more powerful and accessible. This ongoing evolution requires continuous learning and adaptation. Stay informed about new technologies, emerging threats, and evolving best practices. What works today may need modification tomorrow as technology landscape shifts. Flexibility and willingness to adapt security and privacy measures ensures ongoing protection as circumstances change.
Remember that perfect security doesn’t exist—every security measure involves tradeoffs among protection levels, convenience, cost, and privacy. Your goal isn’t achieving impossible absolute security but rather implementing reasonable protections matching your specific risk profile and needs. Small, consistent security practices often provide better protection than elaborate systems that get abandoned because they’re too burdensome.
Privacy protection similarly requires ongoing attention rather than one-time actions. Regular reviews of privacy settings, awareness of surroundings, and appropriate use of privacy tools maintain protections as technology and circumstances evolve. The techniques and tools we’ve discussed provide foundation, but applying them consistently in daily life makes them effective.
Most importantly, trust your instincts and take concerns seriously. If situations make you uncomfortable, remove yourself rather than ignoring warning feelings. If something seems wrong with accommodations, conduct security checks or request different rooms. If you discover unauthorized surveillance, report it to appropriate authorities rather than handling it privately. Your safety and privacy are worth protecting, and concerns deserve serious response.
The path forward involves education, awareness, appropriate tool selection, consistent practice, respect for others’ rights, and balance between security and privacy. By understanding the technologies, recognizing appropriate uses and misuses, implementing proportionate protections, and maintaining ethical practices, you can successfully navigate our technologically complex world while protecting yourself and respecting others.
Your security and privacy journey is personal and ongoing. Take what you’ve learned here and adapt it to your specific circumstances, risks, and values. Whether you’re implementing new security measures, becoming more aware of privacy risks, or simply better understanding the technology surrounding us all, you’re now better equipped to make informed decisions protecting yourself and loved ones while participating responsibly in our increasingly interconnected world.
Security and privacy in the digital age require active participation rather than passive acceptance. Take control of your security through knowledge, appropriate tools, and consistent practices. Protect your privacy through awareness, vigilance, and proactive measures. Balance protection with respect for others’ rights. The power to secure yourself and maintain privacy is in your hands—use it wisely and responsibly.
Frequently Asked Questions
Q: Is it legal to use hidden cameras in my home? Generally yes, you can use security cameras in your own home, but there are important restrictions. You cannot place cameras in areas where people have reasonable privacy expectations—bathrooms, bedrooms used by guests, changing areas. If you employ nanny cams or home security cameras, many jurisdictions require disclosing surveillance to employees or guests. Recording audio often has stricter rules than video—check local laws. Never record guests in private areas without explicit consent.
Q: Can I legally track my spouse’s car with GPS? Laws vary by jurisdiction. Even if you jointly own the vehicle, secretly tracking your spouse without knowledge may violate privacy laws in many locations. Some states consider such tracking a form of stalking or harassment. If you’re concerned about a partner’s activities, address concerns through direct communication rather than covert surveillance. Always research specific laws in your location before deploying GPS tracking on any vehicle you don’t solely own.
Q: How can I detect if someone is tracking my car? Check vehicle undercarriage, wheel wells, bumpers, and interior spaces for unfamiliar devices—GPS trackers are often magnetic and attach to metal vehicle components. Look for small boxes or devices that seem out of place. RF signal detectors can identify trackers transmitting location data. Professional bug sweeps by security specialists provide thorough detection if you have serious concerns. Also monitor for signs like someone knowing your whereabouts without explanation or unfamiliar vehicles following you.
Q: Are spy cameras in hotel rooms common? While disturbing incidents receive significant media attention, hidden cameras in hotel rooms remain relatively rare. However, they do occur, making basic security checks worthwhile. Focus detection efforts on Airbnb rentals and budget accommodations where oversight is less stringent than major hotel chains. Conduct visual inspection of rooms, particularly smoke detectors, clocks, and devices positioned to view beds or bathrooms. Use smartphone detection methods to scan for camera lenses and infrared LEDs.
Q: What should I do if I find a hidden camera? Don’t touch or move the device—preserve evidence showing its position and characteristics. Take photos documenting the camera, its location, and context clearly showing it’s surveillance equipment in private space. Contact police immediately to file report—hidden cameras in private spaces are illegal in most jurisdictions. Leave the accommodation if possible. Contact hotel management or Airbnb about the violation. Save all communications and consider consulting an attorney about potential legal action for privacy violation.
Q: Can employers legally use cameras to monitor employees? Generally yes, employers can monitor workplaces with cameras, but restrictions apply. Cameras cannot be placed in bathrooms, changing rooms, or other private spaces. Most jurisdictions require notifying employees about workplace surveillance even when it’s legal. Audio recording of conversations often requires consent even when video monitoring is permitted. Monitoring should be for legitimate business purposes like security or productivity, not for inappropriate purposes like harassment.
Q: Are personal alarm devices effective? Yes, personal alarms can be very effective for safety. The loud sound (typically 120+ decibels) startles attackers and alerts others to danger. Alarms work best in populated areas where loud noises attract attention and potential help. In isolated areas with no one nearby to hear alarms, they mainly serve to startle attackers potentially creating opportunity to escape. Combine personal alarms with other safety measures like awareness, avoiding dangerous situations, and having emergency contacts readily available.
Q: Do RF signal detectors really find hidden cameras? RF detectors can find hidden cameras that transmit wirelessly—WiFi cameras, cellular cameras, Bluetooth cameras. They detect radio frequency signals these devices emit when transmitting. However, RF detectors won’t find cameras that only record locally without transmitting, which some hidden cameras do to avoid detection. For comprehensive detection, combine RF detection with visual inspection, camera lens detection, and infrared detection methods. Professional detection equipment provides more reliable results than consumer-grade detectors.
Q: How long do GPS tracker batteries last? Battery life varies enormously based on tracker type and usage. Real-time trackers transmitting location continuously typically last 3-14 days. Motion-activated trackers that only transmit when devices move can last weeks or months. Hardwired trackers connecting to vehicle power supplies last indefinitely. Some trackers include user-replaceable batteries while others require recharging. Check specifications carefully when purchasing trackers, ensuring battery life matches your intended use patterns.
Q: Can I use a VPN to protect privacy on public WiFi? Yes, VPNs provide crucial protection on public WiFi networks. They encrypt all data between your device and VPN servers, preventing interception by others on same network or network operators. Without VPN protection, public WiFi can expose passwords, financial information, and browsing activity. Use reputable VPN services with strong encryption and no-logging policies. Enable VPN connections before accessing any sensitive information on public networks. However, VPNs don’t protect against device-level threats like malware—maintain other security measures alongside VPN use.
Articles related:
Tags
📧 Get More Articles Like This
Subscribe to receive product reviews and buying guides in your inbox!
We respect your privacy. Unsubscribe at any time.




